The VRF Challenge: Determinism Meets Vulnerability
Verifiable Random Functions (VRF) are cryptographic engines powering Web3’s fairness — from blockchain lotteries to DAO governance. They generate deterministic randomness tied to a secret key (SK):
Offchain Random Generator:
random_number = VRF_HASH(SK, input)
signature = VRF_SIGN(SK, random_number)
Onchain Contract Validation:
VRF_VALIDATE(PK, signature)
The TEE (Trusted Execution Environment) traditionally hosts this SK, leveraging hardware isolation for security. But such implementations face critical limitations:
- Key Immutability: Hardware compromise ⇒ permanent key leakage
- Hardware Dependency: TEE failure ⇒ service termination (single points of failure)
Phala’s dstack-kms: Blockchain-Controlled Secret Derivation
Phala Flash VRF uses dstack-kms, which fundamentally transforms encryption key management in confidential computing. Unlike hardware-bound approaches, it generates a unique, stable Application Key for each application based on its code and configurations. This Application Key serves as the cryptographic foundation for:
- Secure data encryption
- Verifiable random number generation
The revolutionary shift:
Hardware-Bound Keys → dstack-kms
│ │
Static/Immutable Dynamic/Portable
│ │
Single Point of Failure → Censorship-Resistant
Core breakthroughs:
-
Hardware Decoupling
Deliberately separates key generation from TEE hardware, enabling encrypted data migration between TEE instances with authorized decryption.
-
Threat-Aware Design
Acknowledges TEE compromise risks through:
- Comprehensive key rotation (backward + forward secrecy)
- Minimal data exposure during migration
- Governance-controlled secret derivation
-
Persistent Root-of-Trust
Maintains verifiability and availability as the system’s foundational layer, even when individual TEE instances fail.
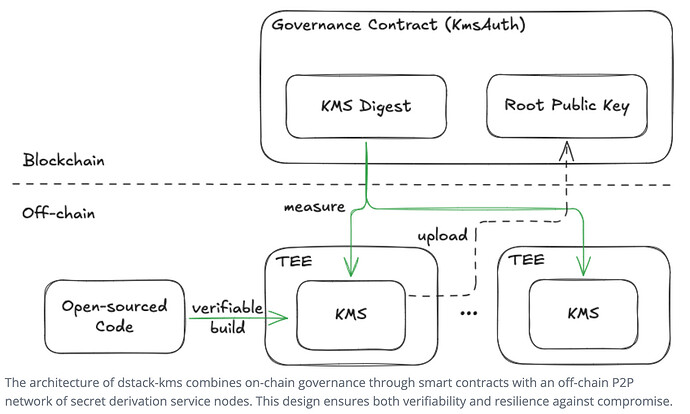
Architectural Implementation
dstack-kms achieves hardware-agnostic key management through three foundational components:
1. Redundant Key Replication
- Active-active secret sharing across multiple TDX-enabled nodes
- Future MPC integration roadmap: Threshold signatures (t-of-n) for enhanced security
2. Deterministic Key Derivation
Root keys are generated cryptographically from immutable application metadata:
3. Hybrid Consensus Mechanism
- On-Chain Governance + Off-Chain P2P Network:
- On-chain: Governance smart contract controls policies.
- Off-chain: Light-client nodes sync secrets via P2P.
VRF Solution Capability Comparison
| Capability | Chainlink VRF | Traditional TEE VRF | Phala Flash VRF |
|---|---|---|---|
| Key Management | |||
| Recovery Time | |||
| Execution Environment | |||
| Key Rotation | |||
| Data Latency | |||
| Cost Sustainability | |||
| Chain Support | N/A |
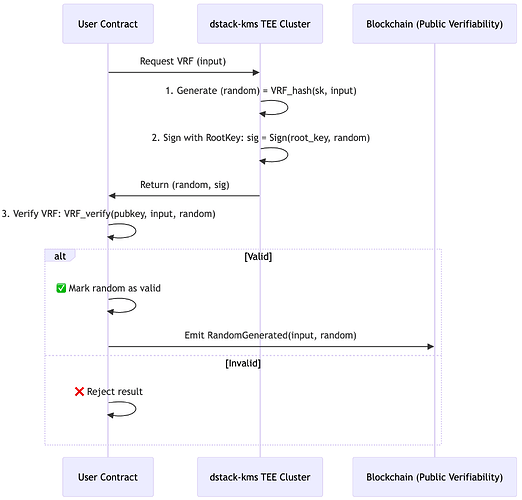
Verification Workflow: End-to-End Verifiable Randomness
Phala’s Flash VRF leverages a triple-layer verification system where cryptographic trust is established through off-chain computation with on-chain validation. Here’s the complete technical workflow:
Key Verification Steps:
- Signature Validation: Confirms response originated from attested enclave
- VRF Validation: Cryptographically verifies output corresponds to input
- State Transition: Only valid outputs modify contract state
Failure Recovery Mechanism
When a TEE node unfortunately crashes:
- Backup nodes reconstruct the key in seconds with the same App-id.
- User requests reroute — zero downtime.
Conclusion: Advancing Flash VRF Resilience
Phala’s dstack-kms demonstrates how cryptographic key derivation combined with trusted execution environments can overcome fundamental limitations in existing VRF implementations. By:
- Decoupling keys from specific hardware instances
- Implementing governance-controlled key rotation
- Leveraging TDX remote attestation
We establish a new standard for verifiable randomness that maintains:
- Fast Response via TEE-generated keys
- Cryptographic integrity through application-bound keys
- Service continuity via rapid failover mechanisms
- Verifiable trust via on-chain validation
The solution provides particular value for applications requiring:
- Real-time response(e.g., real-time gaming, high-frequency trading)
- High-availability randomness (e.g., gaming, lotteries)
- Regulatory-compliant operations (e.g., RWA tokenization)
- Cross-chain compatibility (EVM and beyond)
Further reading: Dstack: A Zero Trust Framework for Confidential Containers
Phala Flash VRF’s Implementation: GitHub - Phala-Network/phala-cloud-vrf-template