It would be useful to have a local devnet environment for e2e testing BuilderNet images.
An initial setup could look like this, with these local components:
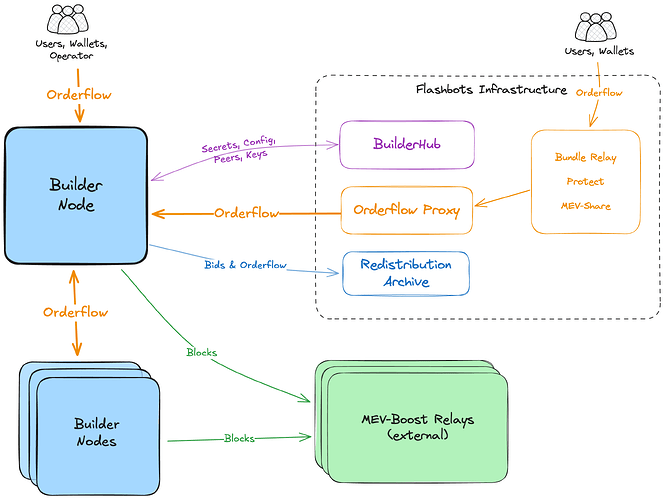
| Builder Playground | Provides the L1 network (EL + CL + MEV-Boost-Relay). No changes needed. |
| BuilderHub service | The builder image gets configuration and secrets from it, and won’t start without it. The only change to this service is to allow all measurements (could be a simple env var DEV_ALLOW_ALL_MEASUREMENTS) |
| BuilderNet Yocto Image | The TDX VM image for the builder node. Needed changes might include additional configuration for Reth and Rbuilder to enable a custom chain, and to skip the chain download step. |
Additional steps (for later phases) might include:
- contender for transactions generation
- orderflow-proxy to send transactions to the BuilderNet instance
- vTPM for disk encryption (optional)
See also the documentation:
Production Architecture Overview
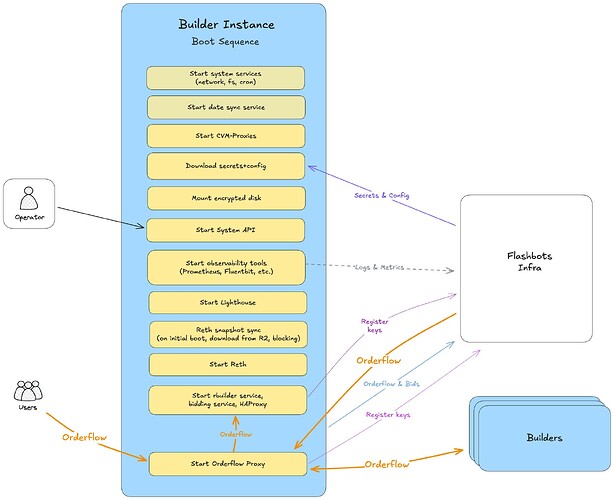
Production Boot Sequence
Initial (incomplete) recommended steps:
- Check out Builder Playground and run it (to get familiar with it)
- Run BuilderHub (read the full README) and play with it’s API (see also API code here)
- Build a BuilderNet Yocto image, with the following modifications:
- Bake in your SSH key (and possibly SSH enabled by default)
- Change the BuilderHub URL to the new local one
- Disable Reth snapshot sync
- Update EL (Reth) and CL (Lighthouse) settings to with with those of the Devnet
- Start the BuilderNet VM image locally with QEMU, and log in with SSH
- It will fail at download secrets+config
- Update BuilderHub
- Allow all measurements (just needs to expect an empty measurements json)
- Enable that builder and add configuration for it
- At this point, downloading secrets + config should already work